The essence of IT governance is in the selection and application of security controls that adequately protect organizational data while simultaneously minimizing operational friction or disruption. The continuum of security controls extends over three classes or categories:
- Management (administrative) controls: Policies, standards, processes, procedures, and guidelines set by corporate administrative entities (e.g., executive- and/or mid-level management)
- Operational and physical controls: Operational security (execution of policies, standards and processes, education and awareness) and physical security (facility or infrastructure protection)
- Technical (logical) controls: Access controls, identification and authentication, authorization, confidentiality, integrity, availability, and nonrepudiation
These controls should be deployed while keeping in mind what I call the Prevent-Detect-Recover cycle.
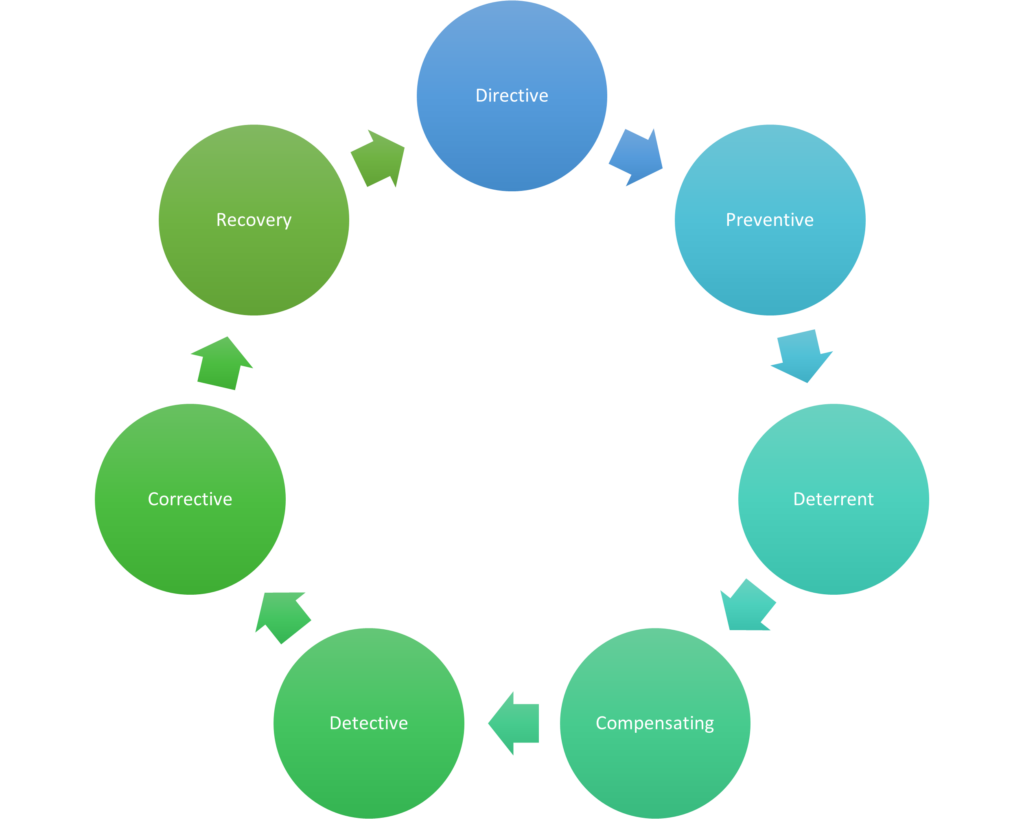
The idea is to prevent what you can, detect what you can’t prevent, and recover (successfully) from what you can’t either prevent or detect. Every time you go through a cycle like this, it should also translate into Directive controls that ensure that you don’t get bit twice. You can achieve PDR mastery by putting the following controls in place:
- Directive controls: Often called administrative controls, these are intended to advise employees of the behavior expected of them during their interfaces with or use of the organization’s information systems
- Preventive controls: Included in preventive controls are physical, administrative, and technical measures intended to preclude actions violating policy or increasing risk to system resources
- Deterrent controls: Deterrent controls involve the use of warnings of consequences to security violations
- Compensating control: Also called an alternative control, a mechanism that is put in place to satisfy the requirement for a security measure that is deemed too difficult or impractical to implement at the present time
- Detective controls: Detective controls involve the use of practices, processes, and tools that identify and possibly react to security violations
- Corrective controls: Corrective controls involve physical, administrative, and technical measures designed to react to the detection of an incident to reduce or eliminate the opportunity for the unwanted event to recur
- Recovery controls: Once an incident occurs that results in the compromise of integrity or availability, the implementation of recovery controls is necessary to restore the system or operation to a normal operating state