It is important to understand the capabilities and policies of your supporting vendors. Emergency communication paths should be established and tested with all vendors.
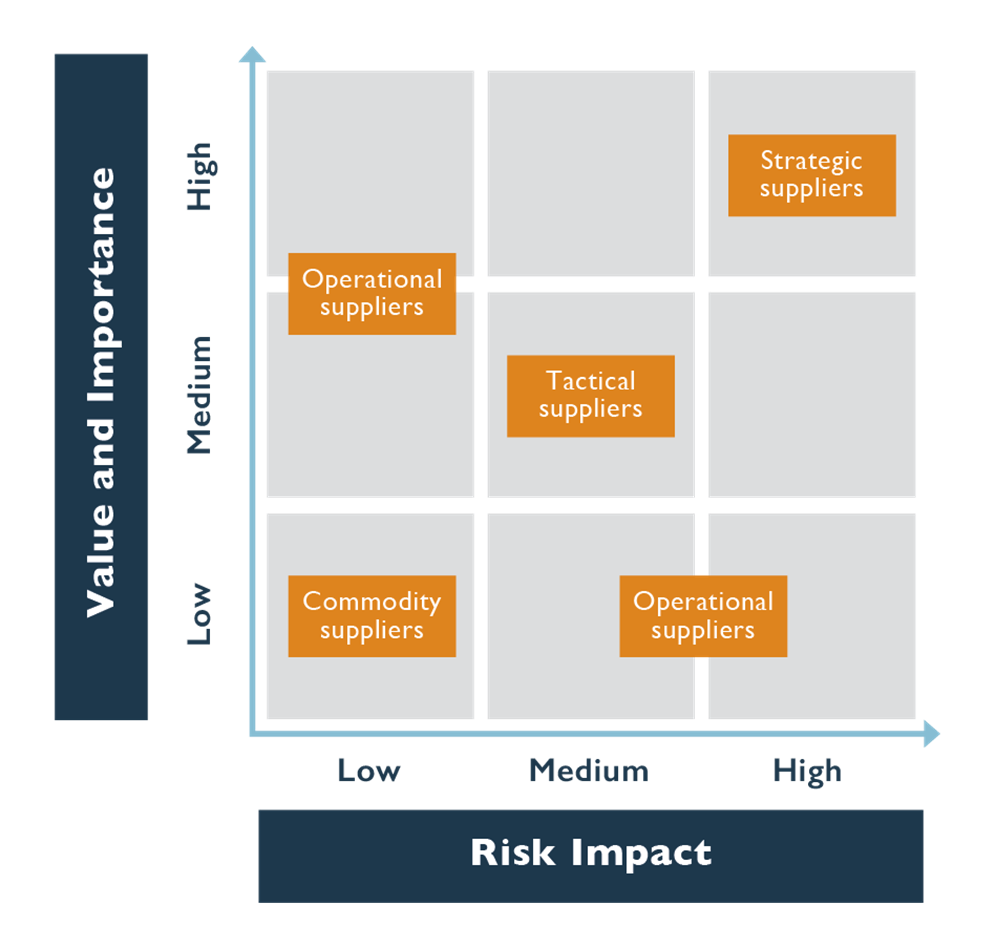
Categorizing, or ranking, a vendor/supplier on some sort of scale is critical when managing the relationship with that vendor/supplier appropriately.
Strategic suppliers are deemed to be mission critical and cannot be easily replaced if they become unavailable. While you will typically do business with very few of these types of partners, they are the most crucial to the success or failure of the enterprise cloud architecture.
Commodity suppliers on the other hand provide goods and services that can easily be replaced and sourced from a variety of suppliers if necessary.
Tactical suppliers supplement strategic and commodity suppliers to manage emerging unforeseen issues and incidents.
Supply-Chain Management
ISO/IEC 27036–4:2016: Information technology — Security techniques — Information security for supplier relationships — Part 4: Guidelines for security of cloud services is not designed to address security controls, business continuity, and other information risk concerns, but is a guideline for:
1) gaining visibility into the information security risks associated with the use of cloud services and managing those risks effectively
2) responding to risks specific to the acquisition or provision of cloud services that can have an information security impact on organizations using these services.
Cloud computing increases the reliance on third parties and approved providers, meaning it needs a steady supply of services and resources to function. This is known as the supply chain. The key component the supply chain introduces is risk; not only can it transfer or reduce certain components of risk (dependent on the organization), but it can create increased risk too.
When looking at supply chain risk, a business continuity and disaster recovery mindset and viewpoint should be taken. A clear and concise listing of all interdependencies and reliance on third parties coupled with the key suppliers should be obtained and regularly updated. Where single points of failure exist, these should be challenged and acted upon to reduce outages and disruptions to business processes.
Organizations need to supplement existing efforts to obtain assurance from contracts where valuable, at-risk information is shared. They need a way to quickly prioritize hundreds or thousands of contracts to determine which of them, and which of their suppliers’ suppliers, pose risk. Based on these documented third parties, a risk review should be undertaken to identify, categorize, and determine the current exposure or overall risk ratings. Compare the results to corporate policies to determine how these risks will be acted upon. Engagement with key suppliers is crucial at this point to ensure that contracts cover such risks, or provide a right-to-audit clause to ascertain and measure relevant risks.
Informed organizations should always prevent deformed risk management practices—this mindset should always be taken when dealing with cloud computing risks.
A brief list of activities that may illuminate risks includes:
- Initial scoping of requirements
- Market analysis
- Review of services
- Solutions assessment
- Feasibility study
- Supplementary evidence
- Competitor analysis
- Risk review/risk assessment
- Auditing
- Contract/service-level agreement review
- Penalty clauses/breach of contract