Previous article in series – Data Security: The Secure Data Lifecyle
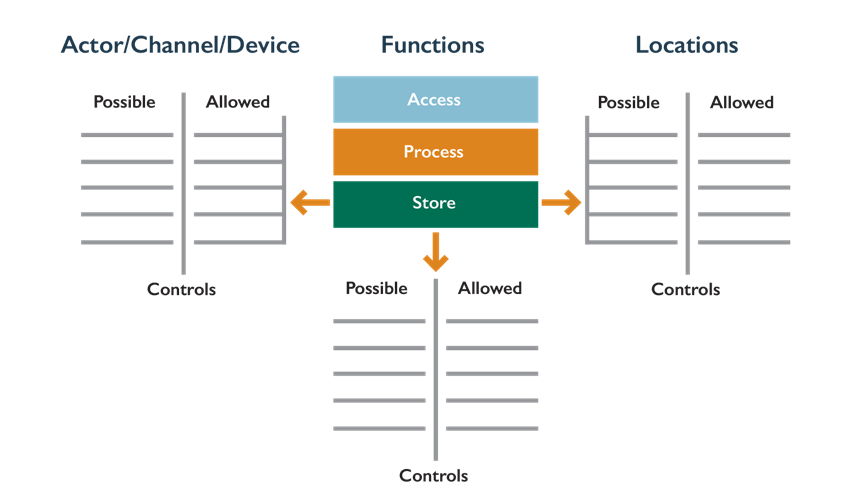
Upon completion of mapping the various data phases, along with data locations and device access, it is necessary to identify what can be done with the data (i.e., data functions) and who can access the data (i.e., the actors). It is also important to consider how to map how nonperson entities (NPE) will use data as well. When addressing specific actor scenarios, applicable device characteristics and the communications channel being used must be taken into account. From a device point of view, the organization may have more effective controls in place if the actor is using a smartphone that’s owned and managed by the organization’s mobile device management software. Similarly, a smartphone connecting to enterprise data over the public internet with TLS encryption may be more vulnerable than the same smartphone communication using enterprise-installed and -managed VPN software.
Once this has been established and understood, controls will need to be checked to ensure which actors have permissions to perform relevant data functions from various locations.
Key Data Functions
Actors can perform the following key functions on data:
- Access: View/access the data, including copying, file transfers, and other exchanges of information
- Process: Perform a transaction on the data (update it, use it in a business processing transaction, etc.)
- Store: Store the data (in a file, database, etc.)
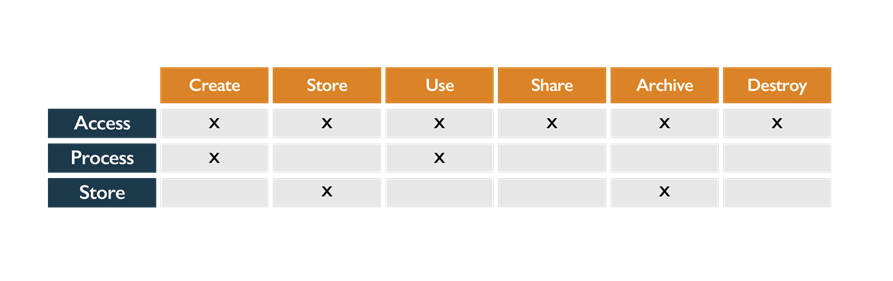
Following figure shows how the functions map to the data lifecycle. Note that each of these functions is performed in a location by an actor (person or NPE).
Controls
Essentially, a control acts as a mechanism to restrict a list of possible actions down to allowed or permitted actions. For example, encryption can be used to restrict the unauthorized viewing or use of data, application controls to restrict processing via authorization, and digital rights management (DRM) storage to prevent copying or accessing of data by untrusted or unauthorized parties.
To determine the necessary controls to be deployed, you must first understand:
- Function(s) of the data
- Location(s) of the data
- Actor(s) upon the data
- Channel(s) transferring the data
- Device(s) accessing the data
Once these items have been documented and understood, then the appropriate controls can be designed and applied to the system in order to safeguard data and control access to it. These controls can be of a preventative, detective (monitoring), or corrective nature.
Next article in series – Data Security: Access Control
2 thoughts on “Data Security: Functions, Actors, and Locations”