The management plane controls the entire infrastructure. Parts of it will be exposed to customers independent of network location, so it is a prime resource to protect. Its graphical user interface, command line interface (if any), and API need to have stringent and role-based access control. In addition, logging of all relevant actions in a logging system is highly recommended. This includes machine image changes, configuration changes, and management access logging. Proper alerting and auditing of these should be considered and governed.
The management plane components are among the highest risk components with respect to software vulnerabilities, as these vulnerabilities can also impact tenant isolation. For example, a hypervisor flaw might allow a guest OS to “break out” and access other tenants’ information or even take over the hypervisor itself. These components, therefore, need to be hardened to the highest relevant standards by following vendor hardening and security guides, including malware detection and patch management.
The isolation of the management network with respect to other networks (storage, tenants, etc.) needs to be considered. Potentially this could be required to be a separate physical network.
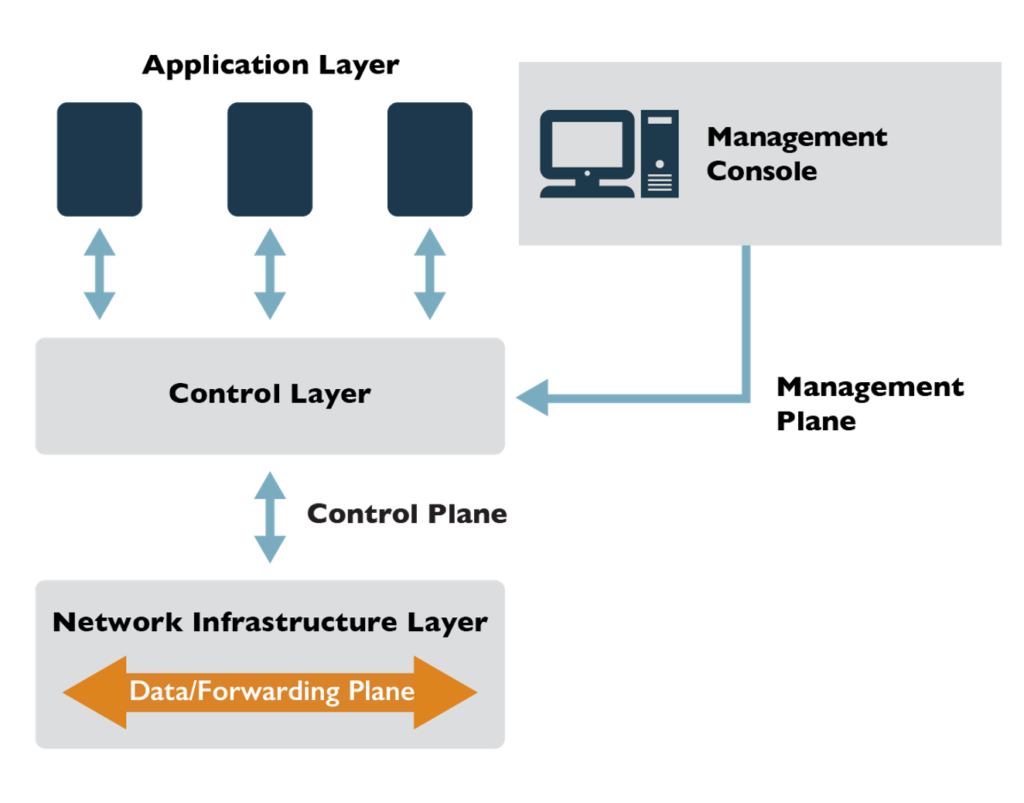
The cloud provider is solely responsible for ensuring the management plane is secure and necessary security features are exposed to the cloud consumer, such as granular entitlements to control what someone can or cannot do. These services are exposed to each customer in the form of a management console.
The cloud consumer is responsible for properly configuring their management console, as well as for securing and managing their credentials.
Here is an inexhaustive list of generic services that extend from the management plane:
- Self-provisioning
- Key management and encryption
- User management
- Identity and access
- management
- Role-based security
- Financial controls
- API integration
- Automation
- Configuration management:
- Service catalog
- Service and helpdesk
- Communication points of contact
Cloud Orchestration
Cloud orchestration is the end-to-end automation workflow, or process, that coordinates multiple lower-level automations to deliver a resource or set of resources “as a service.”
Cloud orchestration is typically delivered by a cloud management platform (CMP) that includes several layers of functionality, including:
- API and web portal/catalog access layer.
- A service catalog management layer that presents service offerings and allows users or automation processes to customize those service offers in real time before deploying. The services may be completely consumption oriented (an end-user service catalog), or also allow dynamic service design, infrastructure modelling, live sandboxing, and so on.
- An orchestration layer that handles the control, governance, and coordination aspects of the service delivery processes. It interacts via abstractions with underlying resources.
- A resource management layer that handles open and abstracted interfacing to all resources whether they are bare metal servers, networking, virtualization, services, or applications.