Previous article in series – Data Security: Functions, Actors, and Locations
As with most areas of technology, access control is merging and aligning with other combined activities—some of these are automated using single sign-on capabilities, while others operate in a standalone, segregated fashion.
The combination of access control and effective management of those technologies, processes, and controls has given rise to identity and access management (IAM). In a nutshell, IAM includes people, processes, and systems that are used to manage access to enterprise resources. This is achieved by assuring that the identity of an entity is verified (who are they, can they prove who they are) and then granting the correct level of access based on the assets, services, and protected resources being accessed.
IAM typically looks to utilize a minimum of two, but preferably three or more, factors of authentication. Within cloud environments, services should include strong authentication mechanisms for validating users’ identities and credentials. In line with best practices, one-time passwords should be utilized as a risk reduction and mitigation technique.
Authorization and Access Management
The traditional data lifecycle model does not specify requirements for who can access relevant data, nor how they are able to access it (device and channels). Access to devices, systems, and resources forms a key driver for use of cloud services (broad network access); without it, we reduce the overall benefits that the service may provide to the enterprise, and by doing so isolate legitimate business or organizational users from their resources and assets.
In the same way that users require authorization and access management to be operating and functioning in order to access the required resources, security also requires these service components to be functional, operational, and trusted in order to enforce security within cloud environments.
In its simplest form, authorization determines the user’s right to access a certain resource (think of entry onto a plane with your reserved seat, or when you may be visiting an official residence or government agency to visit a specified person).
When we talk about access management, we focus on the manner and way in which users can access relevant resources, based on their credentials and characteristics of their identity (think of a bank or highly secure venue—only certain employees or personnel can access the main safe or highly sensitive areas).
Note that both authorization and access management are “point-in-time activities” that rely on the accuracy and ongoing availability of resources and functioning processes (joiner, mover, leaver), segregation of duties, privileged user management, password management, etc., to operate and provide the desired levels of security. If any of the mentioned activities are not carried out regularly as part of an ongoing managed process, this can weaken the overall security posture.
Provisioning and Deprovisioning
Provisioning and deprovisioning are critical aspects of access management—think of setting up and removing users. In the same way you would set up an account for a user entering your organization who requires access to resources, provisioning is the process of creating accounts to allow users to access appropriate systems and resources within the cloud environment.
The ultimate goal of user provisioning is to standardize, streamline, and create an efficient account creation process, while creating a consistent, measurable, traceable, and auditable framework for providing access to end users.
Deprovisioning is the process whereby a user account is disabled when the user no longer requires access to the cloud-based services and resources. This is not just limited to a user leaving the organization, but may also be due to a user changing role, function, or department. Deprovisioning is a risk mitigation technique to ensure that “authorization creep” does not occur, meaning additional and historical privileges are not retained, thus preventing access to data, assets, and resources that are not necessary to fulfill the job role.
Centralized Directory Services
As when building a house or large structure, the foundation is key. In the world of IAM, the directory service forms the foundation for IAM and security both in an enterprise environment and within a cloud deployment. A directory service stores, processes, and facilitates a structured repository of information stored, which is coupled with unique identifiers and locations.
The primary protocol in relation to centralized directory services is lightweight directory access protocol (LDAP), built and focused on the X.500 standard. LDAP works as an application protocol for querying and modifying items in directory cloud service providers.
Essentially, LDAP acts as a communication protocol to interact with Active Directory. LDAP directory servers store their data hierarchically (similar to DNS trees/Unix file structures) with directory records’ distinguished name (DN) read from the individual entries back through the tree, up to the top level.
Each entry in an LDAP directory server is identified through a DN. Access to directory services should be part of the identity and access management solution and should be as robust as the core authentication modes used.
The use of privileged identity management features is strongly encouraged for managing access of the administrators of the directory. If these are hosted locally rather than in the cloud, the IAM service will require connectivity to the local LDAP servers, in addition to any applications and services for which it is managing access.
Within cloud environments, directory services are heavily utilized and depended upon as the “go to” trusted source by the identity and access management framework as a security repository of identity and access information. Again, trust and confidence in the accuracy and integrity of the directory services are a must.
Privileged User Management
As the names implies, privileged user management focuses on the process and ongoing requirements to manage the lifecycle of user accounts with highest privileges in a system. Privileged accounts typically carry the highest risk and impact, as compromised privileged user accounts can lead to significant permissions and access rights being obtained, thus allowing the user/attacker to access resources and assets that may negatively impact the organization.
The key components from a security perspective relating to privileged user management should, at a minimum, include the ability to track usage, authentication successes and failures, and authorization times and dates; log successful and failed events; enforce password management; and contain sufficient levels of auditing and reporting related to privileged user accounts.
Many organizations may monitor this level of information for “standard” or general users, which would be beneficial and useful in the event of an investigation; however, the privileged accounts should capture this level of detail by default, as attackers will often target and compromise a general or “standard user” with the goal of escalating privileges to a more privileged or admin account. A number of the mentioned components are technical by nature, therefore the overall requirements that are used to manage them should be driven by organizational policies and procedures. Note that segregation of duties can form an extremely effective mitigation and risk reduction technique around privileged users and their ability to effect major changes.
Tying It Together
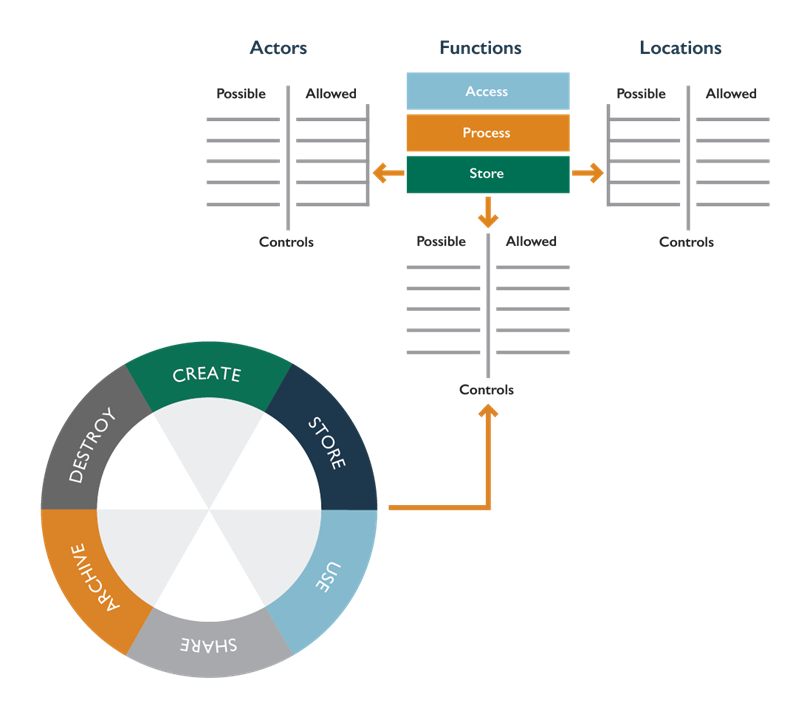
At this point, we are able to produce a high-level mapping of desired data flow controls, including device access and data locations. For each location, we can determine the relevant function and actors. Once this is mapped, we can better define what to restrict from which actor and by which control.
While this may look too complicated for each application, the data security lifecycle can be very useful when discussing the general guidelines for enterprise data governance from a larger viewpoint.
Next article in series – Data Security: Relevant Technologies