In cloud computing, security is a shared responsibility between the CSP and the customer. The service model will dictate the general responsibilities, but specifics will also vary based on the actual service being consumed.
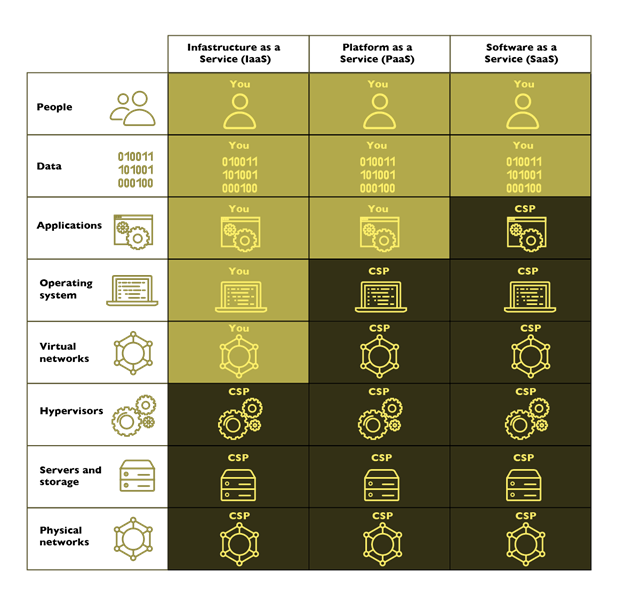
Security Considerations for Infrastructure as a Service (IaaS)
Within IaaS, a key emphasis and focus must be placed on the various layers and components stemming from the architecture through to the virtual components. Given the reliance and focus placed on the widespread use of virtualization and the associated hypervisor components, this forms a key focus as a method or attack vector to gain access to or disrupt cloud service.
The purpose of IaaS infrastructure is to provide standardized compute, memory, network, and storage resources that enable scalability by providing a highly abstracted, shared environment that hosts virtual machines for multiple tenants.
During due diligence, the customer should ensure that security partitions reliably isolate tenants from one another. This isolation must be present throughout all IaaS infrastructure components: host, virtual machine, compute, memory, network, and storage.
When deploying a private cloud IaaS service, the enterprise should enforce a baseline security configuration across all physical hosts. IT governance should require clients to have sufficient security systems such as anti-virus, anti-malware, and up-to-date patches. This should be enforced through robust security mechanisms.
Another important part of due diligence is how network traffic of each tenant’s systems is isolated from the other tenants on the system. Virtual servers connected by virtual network cards to virtual networks should be protected by virtual firewalls.
From the service provider network’s point of view regarding nonaffiliated systems, you can require network encryption. All systems should be isolated logically by taking advantage of network virtualization techniques. For storage services, access control or system authorization will typically be implemented at the operating system level.
Next article in series – IaaS: Hypervisor Security
1 thought on “Cloud Computing: Shared Security Model”