The “intrusion kill chain” framework is an analytical tool introduced by Lockheed Martin security researchers in 2011. It is also sometimes referred to as the “Cyber Kill Chain”. It is an intelligence- driven, threat-focused approach to study intrusions from the adversaries’ perspective that could give network defenders the upper hand in fighting cyber attackers.
So, what is the “kill chain”? It is the chain of multiple steps an attacker must proceed through to plan and execute an attack.
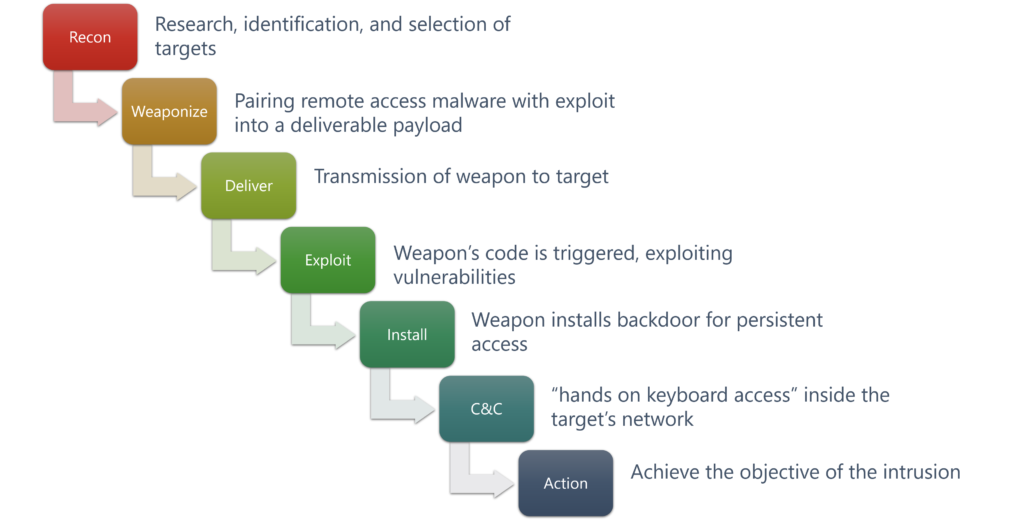
While the attacker must complete all of these steps to execute a successful attack, the defender only has to stop the attacker from completing any one of these steps to thwart the attack.
Analyzing past attacks, utilizing threat intelligence, and improving defenses at all phases of the kill chain allow a defender to detect and deny future attacks earlier and earlier in the kill chain. This requires constant vigilance, but it can theoretically defend against even APTs using so-called “zero-day” exploits, which utilize previously unknown vulnerabilities and attack signatures that defense tools cannot detect.
Even though this model has been criticized for focusing on perimeter security and being limited to malware prevention, when combined with advanced analytics and predictive modeling, it can help strengthen your cybersecurity posture.